What is encryption or data encryption

In a world where thousands of data travel every second over the internet It is important to have a system that allows confidential information to not be read by people other than us.
To ensure that the information we send can only be understood by the correct recipient, encryption algorithms were invented, some mathematical techniques that allow you to hide a message so that only whoever we want can read it.
In this article we will talk about What is encryption, how does it work and what types exist. If you are interested in cybersecurity, stay and discover everything that is hidden behind encryption systems. If you want to know more about cybersecurity you can visit our article on how to study computer security .
Definition of encryption and how it works
Encryption is a set of strategies and methodologies that make use of mathematical algorithms in order to protect the data that circulates through the network to prevent anyone from intercepting it and using it for malicious purposes.
We are increasingly accustomed to using the internet for any task. In recent years, online purchases have increased.
Whenever we make an online transaction, our card information is sent over the network to the bank so that the purchase can be effective.
The internet network is a public place Therefore, people with knowledge of network cybersecurity could intercept bank account information and extract money from them.
The solution to this problem is to encode said information so that if someone manages to intercept it, they will not be able to read or use it. This encoding of the message is called data encryption and only the sender and receiver are capable of decoding this information.
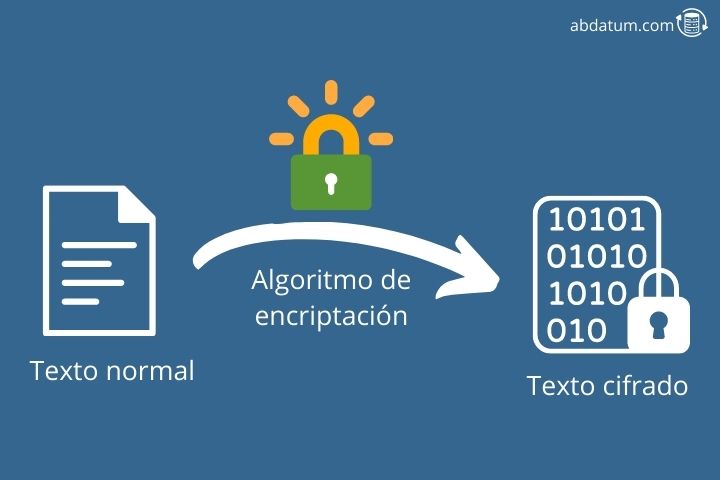
Although today encryption systems are increasingly relevant due to the amount of confidential information that moves through network, messaging encryption is nothing new.
There are multiple situations where humans have needed to encrypt messages to prevent other people from understanding them. We find examples from ancient Egypt to World War II.
I recommend watching the movie Cracking the Enigma where the protagonist Alan Turing (Benedict Cumberbatch) finds a methodology to decipher the encrypted messages of the Germans during the Second World War. The machine used to encrypt the messages was called Enigma.
In this movie you will be able to understand the entire procedure that went into creating a technology that could decrypt those messages.
Types of data encryption or encryption methods
There are 3 basic ways to encrypt data: symmetric, asymmetric and hybrid encryption. Each of these forms includes a group of different encryption algorithms.
Symmetric encryption
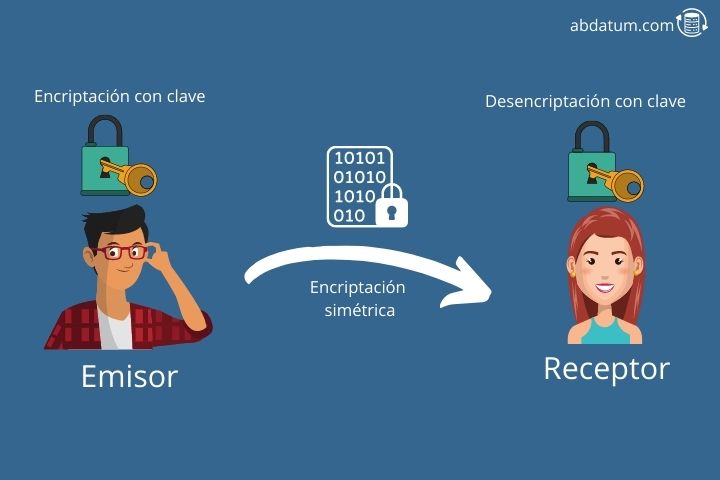
Symmetric encryption It is a cryptographic method where the same key is used both to encrypt and decrypt the message. It is important that both the sender and the receiver know this key. Otherwise they will not be able to understand the message effectively.
In this type of encryption all security lies in the key so it is vitally important that it be almost impossible to remove by brute force. That is to say, if we start trying key combinations, it must be long enough for a computer to take too long to guess it, making it not feasible to decrypt the message.
In the film based on real events that we discussed in the previous section we can see how Enigma used a symmetric cryptographic system to encode German messages.
Asymmetric encryption
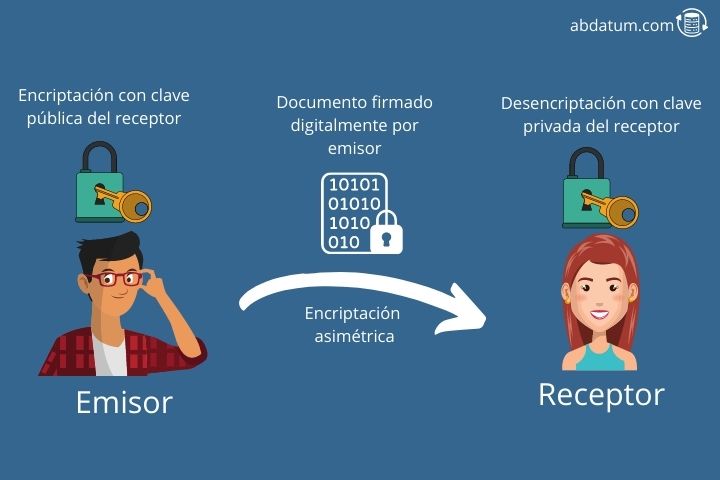
Asymmetric cryptography, also known as two-key or public-key-private-key cryptography, is a type of encryption that Unlike symmetric cryptography, it uses two keys: the public key and the private key.
Everyone can know the public key. On the other hand, the private one is only for us and no one else can know it.
When we want to send an encrypted message to someone, we encrypt it using the receiver's public key since only the receiver with his private key will be able to decrypt the message encrypted with his public key.
This allows us to send the message through an insecure channel since no matter how much someone intercepts it, they will not be able to read the content inside since they do not have the recipient's private key. This allows us to have confidentiality.
Another important property of cryptography is authenticity. To ensure that the sender sending the message is really who they say they are, the message is digitally signed using the sender's private key.
The receiver can authenticate that it is the true sender since it can verify the signature using the sender's public key.
Asymmetric cryptography is slower than symmetric cryptography. However, it is more secure and is the one used to send emails or exchange messages on platforms such as WhatsApp or Telegram.
Hybrid encryption
Hybrid cryptography mixes the previous two to combine the advantages of both methods and eliminate the disadvantages. With this mixture, a more secure encryption method is achieved than symmetric encryption and a faster encryption than asymmetric cryptography.

